Those that are familiar with Software Escrow and its role within business continuity planning can appreciate its immense value when it comes to risk mitigation. However, for those that are unfamiliar with Software Escrow and the range of complex terminology that’s associated with it, it can seem like an overwhelmingly complicated concept.
Truth be told, the concept of Software Escrow (also known as Source Code Escrow) is actually quite simple. Within this blog, we’ll be breaking down some key concepts that are at the core of Software Escrow. Alongside this, we’ll be exploring Software Escrow’s overarching purpose, its implications, and the processes that are involved within its implementation.
Understanding Common Software Escrow Terms
Before we explore what Software Escrow is, we’ll first be looking at 4 common terms that are prevalent within the Software Escrow space:
Critical Application
A critical application may also be referred to as a ‘mission-critical application’ or a ‘business-critical application’).
A critical application is a software application that holds a significantly high level of importance to an organisation. Essentially, this type of application plays a pivotal role in ensuring that business operations are running successfully. As a result, critical applications are heavily relied upon. Examples of such applications include financial transaction software, HR platforms, and database management systems.
Source Code
Within the IT industry, source code is widely regarded as the most foundational component of any software program.
Source code is code that is created by software developers and programmers. It typically follows a format that enables it to be easily and effectively read by humans. Source code determines the behaviour and features of a software application, as well as how it functions.
Release Event
The Software Escrow process involves a trusted Escrow provider, such as SES Secure, testing and securely storing a copy of a software application’s source code.
If an application’s end user faces some form of disruption event which impacts how operational and accessible an application is, their Escrow provider could release a copy of the source code, enabling them to regain access to it. This situation is referred to as a release event.
Software Escrow agreements contain pre-established criteria conditions which when met, can activate a release event. These conditions are widely known as ‘release triggers’ or ‘release conditions’.
Business Continuity
The concept of business continuity refers to an organisation’s ability to manage unexpected operational challenges in a manner that allows the delivery of business activities and operations to remain uninterrupted.
Through prioritising business continuity planning, an organisation can ensure that it’s as well prepared as possible to mitigate against and effectively manage any unforeseen disruption that it encounters.
What is Software Escrow?
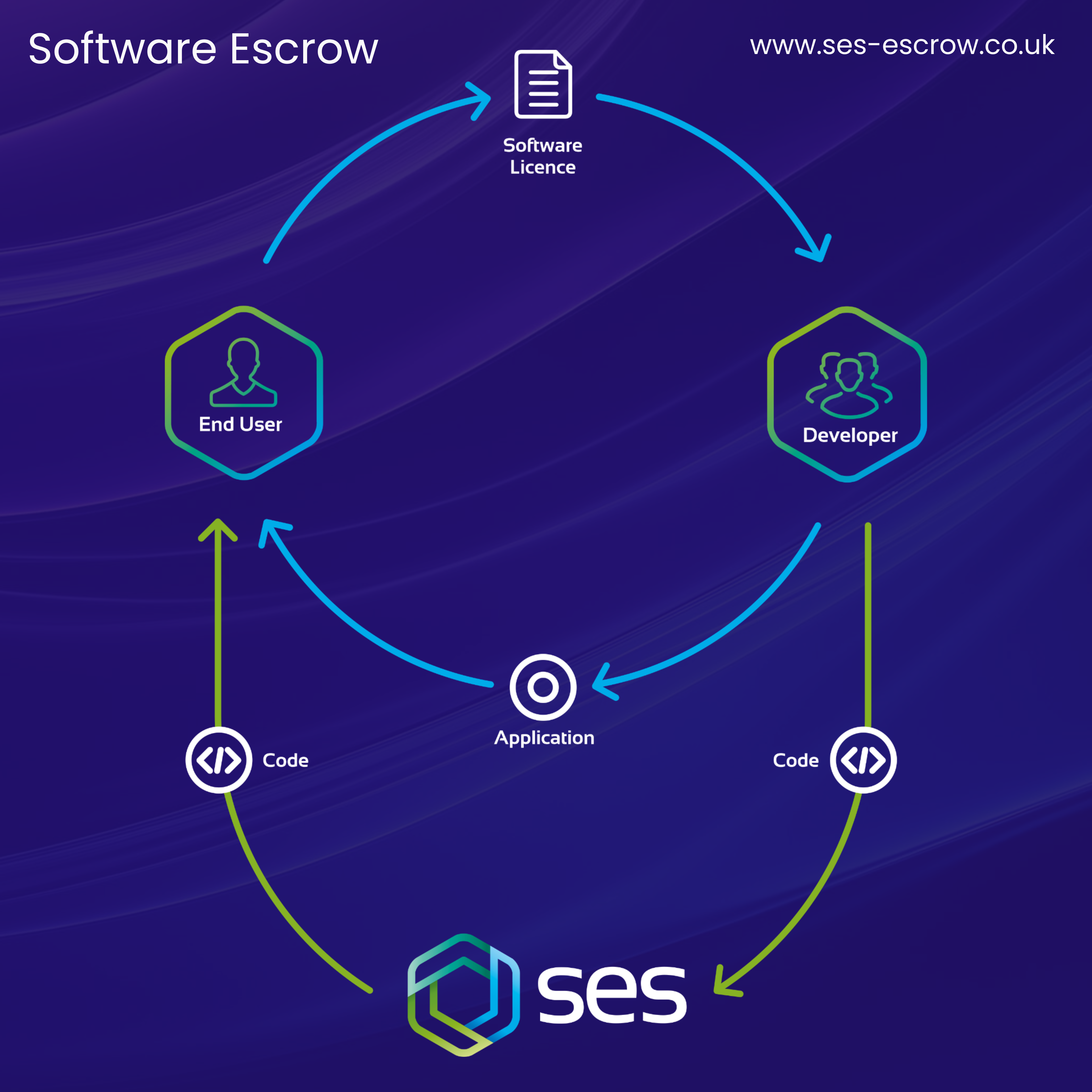
Software Escrow is a risk mitigation tool that safeguards critical applications and supports business continuity. A Software Escrow Solution involves a tri-party legal contract between the following parties:
- An application’s end user – e.g., an organisation that’s seeking to safeguard and futureproof a critical application that they rely on heavily.
- A software supplier (also known as a software vendor) – this is the party that supplies the end user with their critical application’s software.
- A trusted third-party Software Escrow provider, such as SES Secure – a Software Escrow Solution involves an Escrow provider collaborating with both software users and developers.
The origins of Software Escrow can be traced back to the 1980’s. This period saw a substantial spike in the popularity and demand for software. Accompanying this increase in software usage was a correlating increase in the level of risk associated with relying on third-party software suppliers. In response to this, Software Escrow was designed and introduced as a risk mitigation tool to support business continuity.
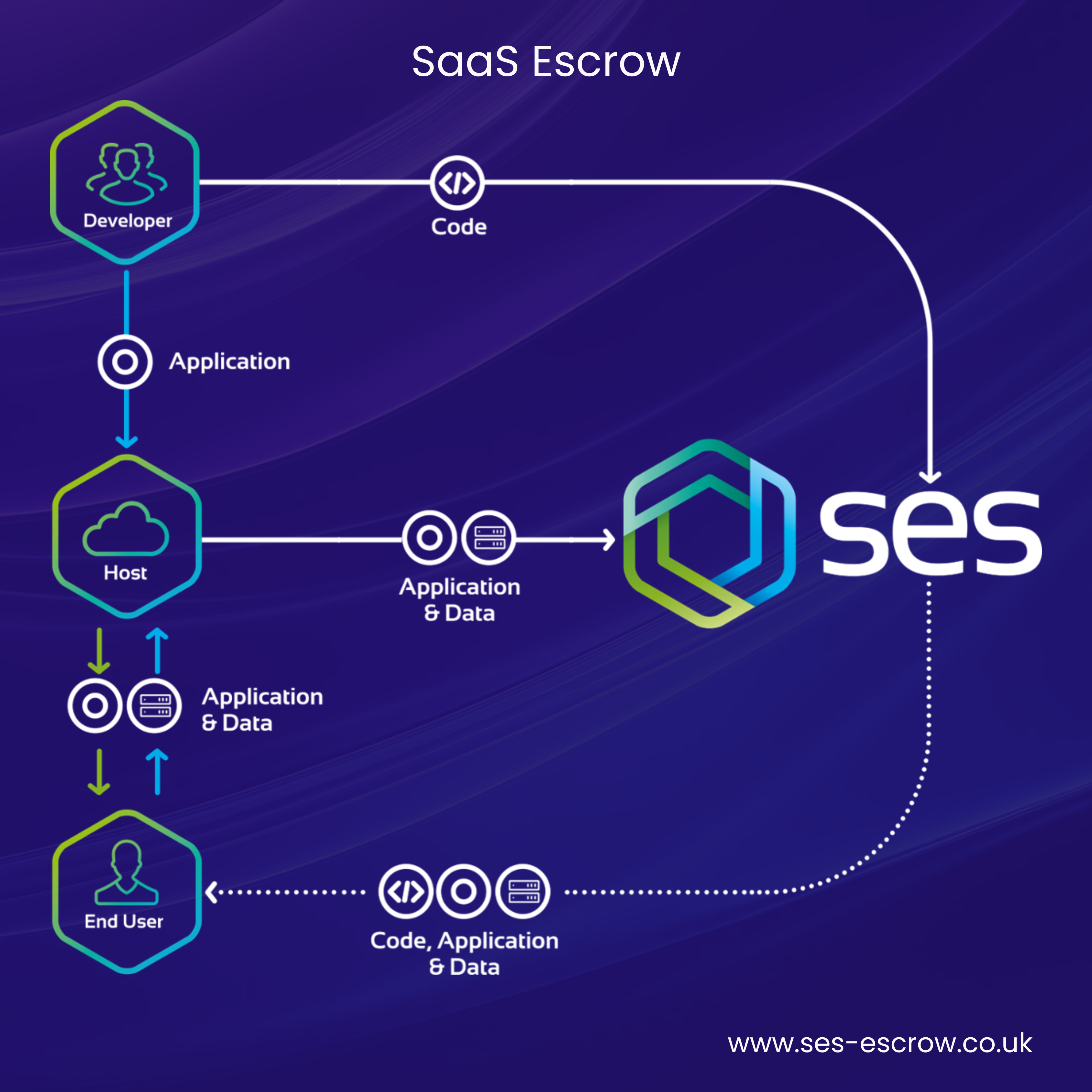
Since the 1980’s, Software Escrow has evolved tremendously. The term ‘Traditional Software Escrow’ refers to solutions that safeguard applications that are installed on-premises. When it comes to modern day Software Escrow, alongside safeguarding on-premises applications, it can also safeguard cloud hosted (SaaS) applications.
The Software Escrow Client Journey at SES Secure
Over the past two decades, we’ve had the pleasure of working with organisations of all sizes from across all industries. Our approach to client projects involves carefully crafting bespoke solutions that meet the specific needs, requirements, and specifications of clients.
Each client journey begins with an initial informal introductory chat. Alongside enabling us to get to know the client, this offers our team a way to identify and determine the best plan of action for the client.
After our team have assessed all possible action plans, these will be discussed with the client. Following this, the Software Escrow implementation process can begin.
See what clients have said about their experiences with us.
To learn more or to schedule a meeting with our team, please get in touch.