The world of software escrow (also known as source code escrow) can certainly be an overwhelming place. Whilst many people recognise the crucial roles of data security and risk management within business management, researching these topics often leads to an abundance of confusing terminology and complex concepts.
Alongside exploring the foundations of software escrow, this blog addresses the ways in which it equips an organisation to be as prepared as possible for operational challenges.
What Is A ‘Critical Application’?
Before delving into software escrow agreements, we must first grasp the importance of critical applications, also known as mission-critical or business-critical applications. In the modern-day digital landscape, a critical application refers to an application that forms a central role within business operations.
Without critical applications, businesses would cease to carry out daily duties and perform at a level that’s in line with their objectives. Examples of critical applications include:
- Data management software
- CRM (customer relationship management) systems
- Financial transaction systems
- Inventory management systems
- HR management systems
If a critical application was to encounter operational challenges, a great deal of risk would be placed on all stakeholders that are impacted by the application. Therefore, the need for a protective risk mitigation measure is paramount for all businesses that use critical applications. This protective solution can be obtained in the form of software escrow.
What is Software Escrow?
So, what actually is software escrow?
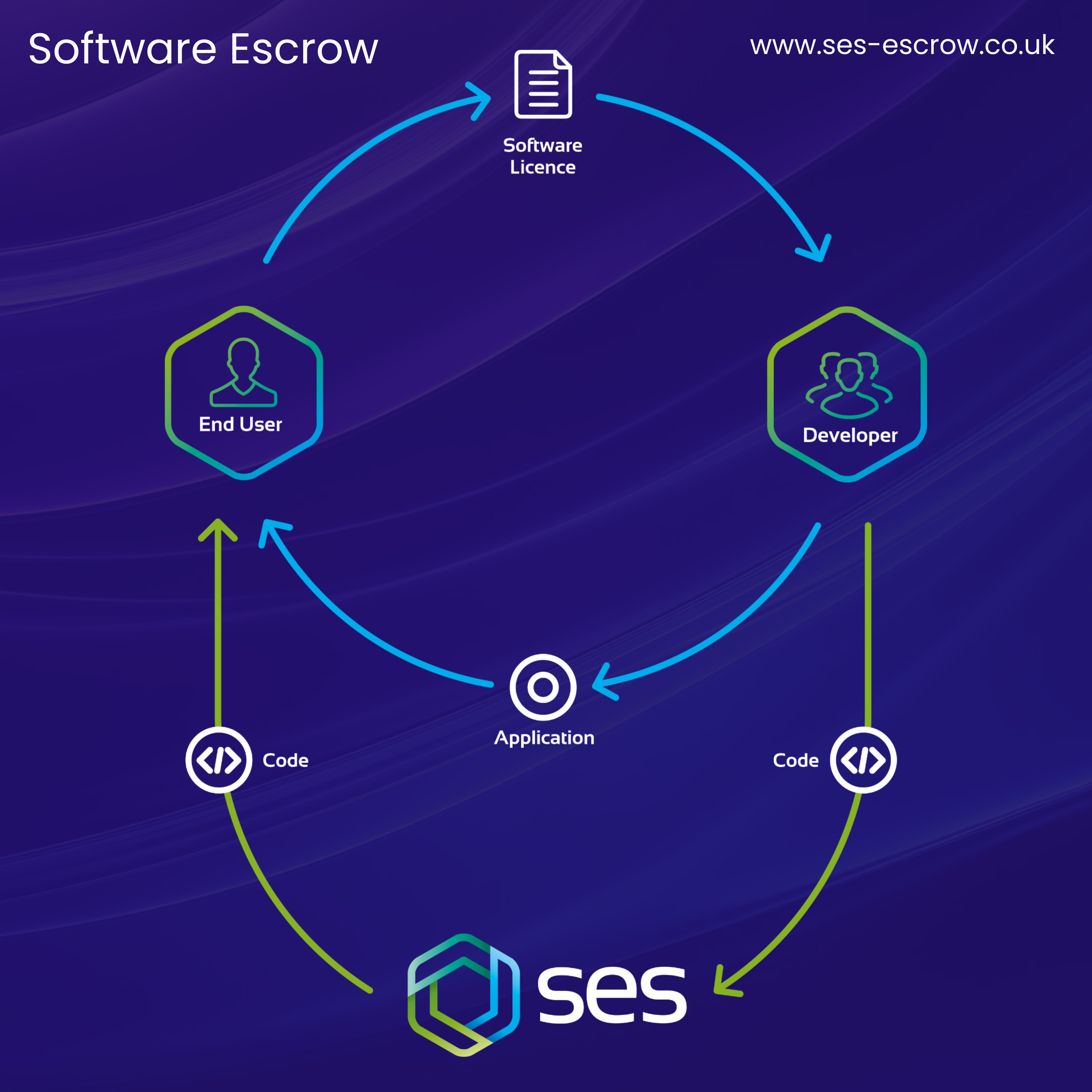
Essentially, a software escrow agreement is a legal agreement between three parties (this is known as a tri-party agreement). The three parties involved are:
- The software owner/supplier (commonly referred to as the vendor)
- The end user (this could be a business’s employees)
- A third-party escrow provider, such as SES Secure
An escrow agreement provides the parties above with the comfort of knowing that a business can demonstrate business continuity despite vendor failure. Business continuity refers to an organisation’s ability to resume the delivery of their products and/or services following an incident that disrupts a critical application.
The agreement enables the organisation to access the software source code in situations where business continuity is at risk. This supports the organisation with continuing business operations, and therefore demonstrating operational resilience.
You may be thinking, ‘what is a source code?’ and ‘what sort of risk does a software escrow agreement protect an organisation from?...well, a source code is a code written by programmers that determines a software application’s behaviour and functionality. Within the IT sector, source code is viewed as the foundation of computer programmes.
The following situations could negatively impact the way that a business is able to use or access a critical application, consequently putting them at risk:
- A software provider encounters maintenance issues.
- A software provider faces bankruptcy or insolvency issues.
- A change in ownership leads to a software provider delivering a different level of service and help.
- A software provider fails to provide effective support during the occurrence of disruptive incidents.
- A software provider goes out of business.
The above situations can jeopardise the ability of a critical application to work, leading to financial loss, operational failure, and reputational damage. The high level of risk associated with these situations can be managed through a software escrow agreement.
When a software escrow agreement is activated, an organisation is provided with a means of continuing its business operations. The agreement enables undisrupted access to critical software applications.
The Importance of Software Escrow
Within many aspects of life, valuable assets are usually protected by some kind of safety net. For example, in addition to locking doors and windows when absent, a homeowner may install an alarm system to deter burglars. Similarly, alongside looking after the condition of an important purchased item, a shopper may also buy insurance cover. This will equip them with a protective solution if a situation arises in which the item becomes faulty, lost or stolen.
Like the examples of the homeowner and the shopper, a business introducing a software escrow agreement presents the introduction of a proactive protection strategy. It also demonstrates a business investing into their ongoing performance and the protection of all stakeholders who are in some way connected to their business.
A software escrow agreement offers an organisation peace of mind from knowing that they can confidently resolve any critical application related issues that they may face.
The SES Software Escrow Agreement Process
The process of strengthening a business’s operational performance through SES Secure’s assistance is one that is built on trust, transparency, and expert support.
Each client is designated a software escrow consultant who is widely experienced in handling complex escrow requirements for our global client base. The role of software escrow varies from client to client. After initial contact from the client, our consultants will determine the specific role that software escrow would play within the client’s organisation (i.e., where, why, and how would it be used?).
Our team will then identify the most effective strategy for meeting client needs and objectives. An agreement will be created and discussed with the software supplier and the end user (the client). Following the agreement of terms, a member of our experienced in-house technology team will witness and document the full build of source code into a working application. If required, our technology will also conduct relevant testing.
After the successful completion of the code validation exercise, the software supplier will deposit source code as well as other required deposited materials. The deposited materials will be held by SES Secure. They are only released when release conditions are met.
In the case of a critical application challenge arising, SES Secure will support a business with ensuring that they are able to continue operating as usual.
Ultimately, a software escrow offers a trusted plan of action for supporting operational resilience in the face of disruption. If you have any further questions or queries, please get in touch. Our team are always at hand to help.